Program
Why is TCP establishing a three-way handshake instead of two or four?
TCP, named Transmission Control Protocol, is a reliable transport layer protocol with an IP protocol number of 6.
By the way, in principle, any data transmission cannot ensure absolute reliability. The three-way handshake is only a basic requirement for ensuring reliability.
To give a daily example, when we make a phone call we have the following dialogue:
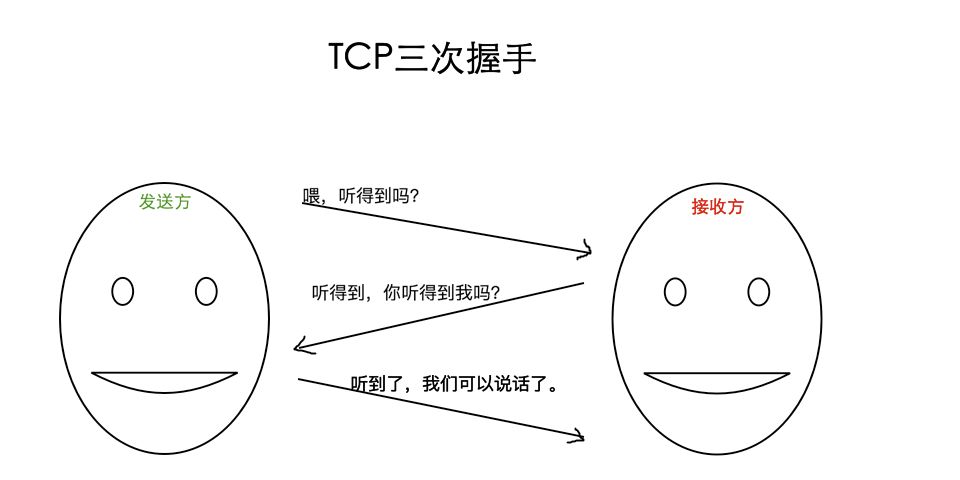
Correspond to the communication between the client and the server:
So we have the following dialogue:
I: What is 1+1?
She: What is 2,2+2?
Me: 4
First two people agree on an agreement
1. When the network situation is wrong, any party can initiate an inquiry
2. In any case, if no response is received within 5 seconds after initiating the inquiry, the network is considered unreachable.
3. Initiate queries after the 1min router waits for a network disconnect
For me, after inquiring "1+1 equals several"
1. If no reply is received within 5s, the network is considered unreachable
2. If I receive a reply, I confirm 1 I can hear her message 2 She can hear my message and reply to the answer to her question
For her, when feeling that the network is not right
1. If she does not receive my inquiry, she initiates an inquiry
2. If "1+1 is equal to several" is received, she confirms that she can hear my message and then reply to the answer to my question and her question "2, 2+2 equals several"
3. If she does not receive my reply "4" within 5s, she confirms 2 I cannot hear her message
4. If she received my reply "4" within 5s, she confirms 2 that I can hear her message
In this way, if the above dialogue is completed, it proves that both parties can confirm that they can hear each other's voice, and the other party can also hear their own voice!
Can this story explain why TCP has to shake three times?
About four waves
The client sends a FIN to the server first, requesting to close the data transmission.
When the server receives the FIN of the client, it sends an ACK to the client, where the value of ack is equal to FIN+SEQ
The server then sends a FIN to the client, telling the client application to close.
When the client receives the FIN from the server, it replies with an ACK to the server. Where ack is equal to FIN+SEQ
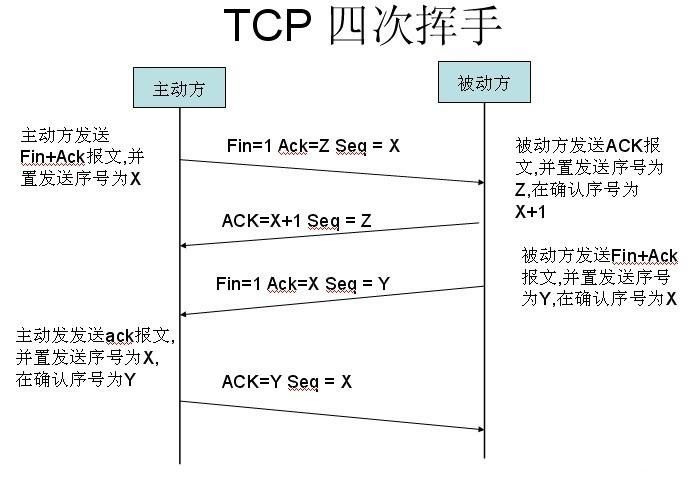
Why do you want to wave 4 times?
Make sure the data can be transmitted completely.
When the passive party receives the FIN message notification from the active party, it only indicates that the active party has no data to send to the passive party.
However, not all data of the passive party are completely sent to the active party, so the passive party will not immediately close the SOCKET. It may also need to send some data to the active party.
Then the FIN message is sent to the active side, telling the active side to agree to close the connection. Therefore, the ACK message and the FIN message are sent separately.
First, TCP message format
TCP packet format:
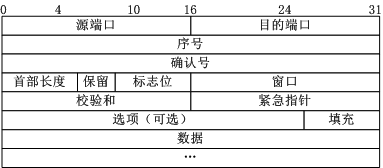
There are several fields in the above figure that need to be highlighted:
(1) Sequence number: Seq sequence number, which occupies 32 bits, is used to identify the byte stream sent from the TCP source to the destination, and the initiator marks this when sending data.
(2) Acknowledgment sequence number: Ack sequence number, accounting for 32 bits. When the ACK flag is set to 1, the sequence number field is validated and Ack = Seq+1.
(3) Flags: A total of six, that is, URG, ACK, PSH, RST, SYN, FIN, etc. The specific meanings are as follows:
(A) URG: Urgent pointer is valid.
(B) ACK: The confirmation sequence number is valid.
(C) PSH: The receiving party should send this message to the application layer as soon as possible.
(D) RST: Reset the connection.
(E)SYN: Initiate a new connection.
(F)FIN: Release a connection.
have to be aware of is:
(A) Do not confuse the confirmation sequence number Ack with the ACK in the flag.
(B) Confirmer Ack = Initiator Req+1, paired at both ends.
Two and three handshakes
TCP (Transmission Control Protocol) Transmission Control Protocol
TCP is a host-to-host layer transmission control protocol that provides a reliable connection service and uses a three-way handshake to establish a connection
The bit code is the tcp flag and there are 6 flags:
SYN (synchronous establishment of online)
ACK (acknowledgement)
PSH (push transfer)
FIN (finish finish)
RST (reset reset)
URG (urgent emergency)
Sequence number
Acknowledge number
Establish Establish, create
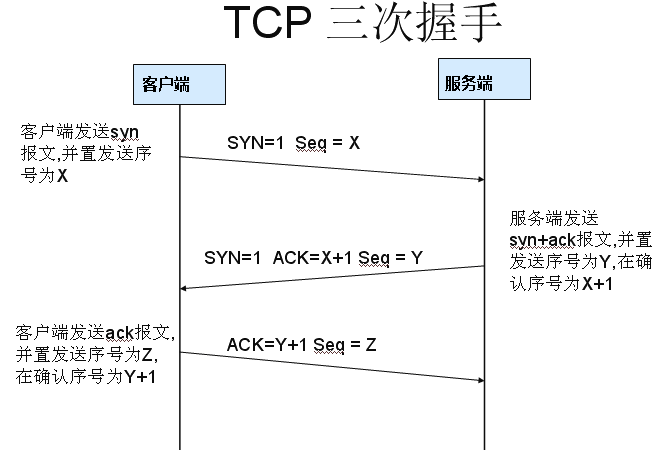
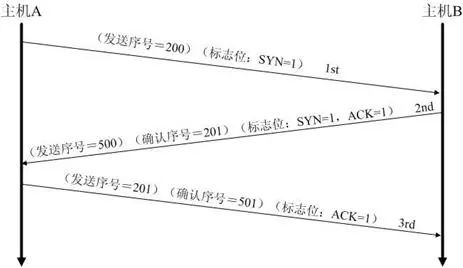
The so-called three-way handshake (Three-Way Handshake) that establishes a TCP connection, refers to the establishment of a TCP connection, the client and the server need to send a total of 3 packets to confirm the establishment of the connection. In socket programming, this process is triggered by the client executing connect. The entire process is shown in the following figure:
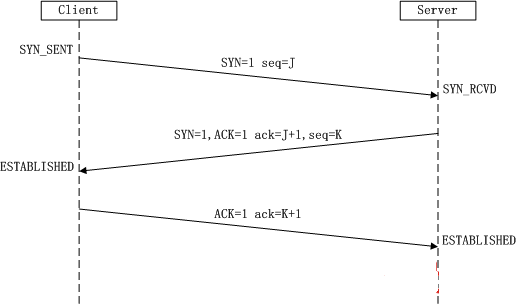
(1) The first handshake: The client sets the flag bit SYN to 1, randomly generates a value seq = J, and sends the packet to the Server. The Client enters the SYN_SENT state and waits for the server to confirm.
(2) The second handshake: After Server receives the data packet, it knows that the client request to establish connection by the SYN bit=1, Server sets the flag SYN and ACK to 1, ack (number )=J+1, randomly generates a The value seq = K, and send this packet to the Client to confirm the connection request, Server enters the SYN_RCVD state.
(3) The third handshake: After the Client receives the confirmation, check whether the ack is J+1, if the ACK is 1, if it is correct, the flag bit ACK is set to 1, ack=K+1, and the data packet is sent. To Server, Server check if ack is K+1, if ACK is 1, if it is correct then connection is established successfully, Client and Server enter ESTABLISHED state, three handshakes are completed, and then Client and Server can begin to transfer data.
SYN attack:
During the three-way handshake, after the server sends the SYN-ACK, the TCP connection before receiving the Client's ACK is called a half-open connect. At this time, the server is in the SYN_RCVD state. After receiving the ACK, the server goes to ESTABLISHED. status. The SYN attack is that the client forges a large number of non-existent IP addresses in a short period of time and continuously sends SYN packets to the server. The server replies with an acknowledgement packet and waits for confirmation from the client. Since the source address does not exist, the server needs to continue to From the time of sending until timeout, these forged SYN packets will occupy the unconnected queue for a long time, resulting in normal SYN requests being discarded because the queue is full, causing network congestion or even system failure. A typical DDOS attack during a SYN attack. The method of detecting a SYN attack is very simple. That is, when there are a large number of semi-connections on the server and the source IP address is random, you can conclude that you have been attacked by a SYN. ​​You can use the following commands to make it. in force:
#netstat -nap | grep SYN_RECV
Three or four waves
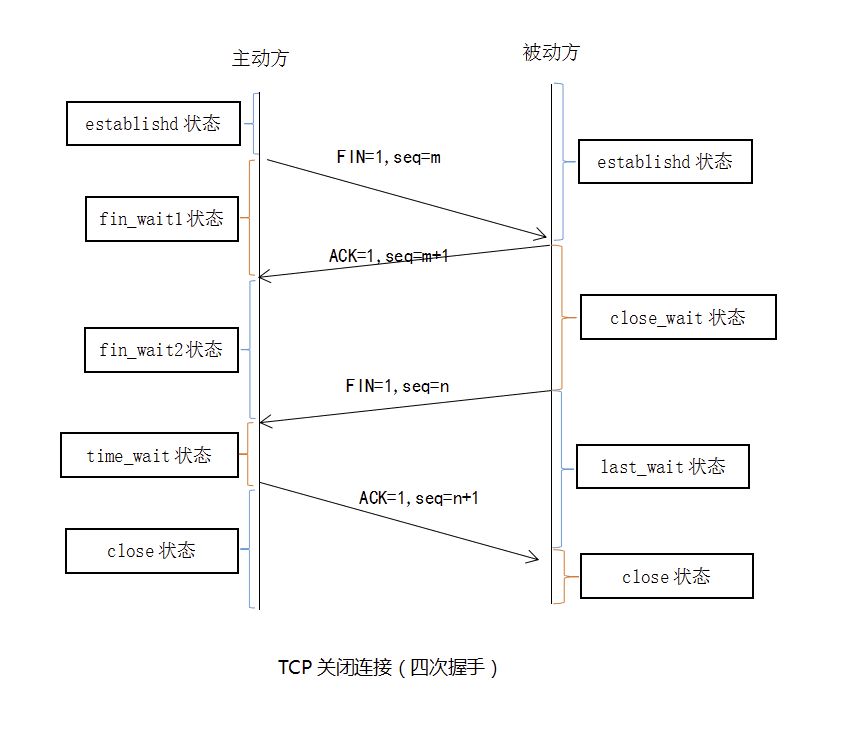
The three-way handshake is familiar, and the four-wave handshake is estimated. The so-called four-way wave (Four-Way Wavehand) terminates the TCP connection, which means that when the TCP connection is disconnected, the client and the server need to send a total of four packets to confirm the connection. disconnect. In socket programming, this process is triggered by the close of either the client or the server, as shown in the following figure:
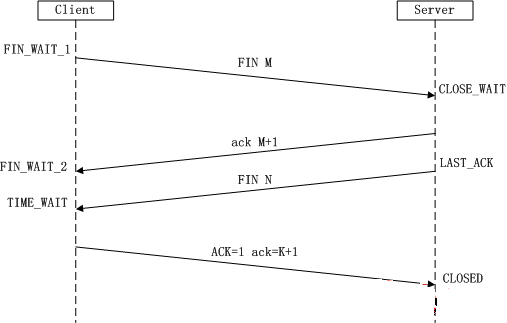
Because the TCP connection is full-duplex, each direction must be closed separately. This principle is that when one party completes the data sending task, it sends a FIN to terminate the connection in this direction. Receiving a FIN just means There is no data flow in this direction, ie no more data will be received, but data can still be sent over this TCP connection until the FIN is sent in this direction. The party that first closed will perform an active close, while the other will perform a passive shut down, as described above.
(1) The first wave: The Client sends a FIN to close the Client to Server data transfer. The Client enters the FIN_WAIT_1 state.
(2) The second wave: After Server receives the FIN, it sends an ACK to the Client, confirming that the sequence number is +1 (same as SYN, a FIN occupies a sequence number), and Server enters CLOSE_WAIT state.
(3) The third wave: Server sends a FIN to close the data transfer from Server to Client. Server enters LAST_ACK state.
(4) The fourth wave: After the Client receives the FIN, the Client enters the TIME_WAIT state, and then sends an ACK to the Server, confirming that the sequence number is the received sequence number+1, and the server enters the CLOSED state and completes four wave operations.
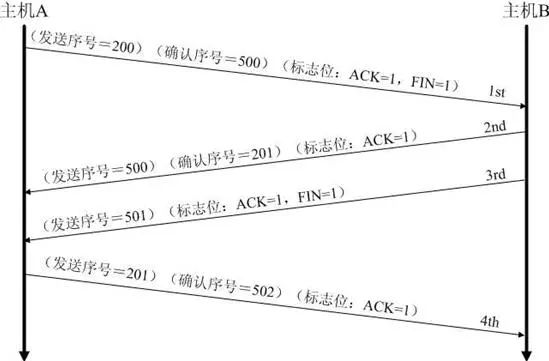
The above is the case where one party voluntarily closes and the other passively closes. Actually, there will also be a case where active close is initiated at the same time. The specific flow is as follows:
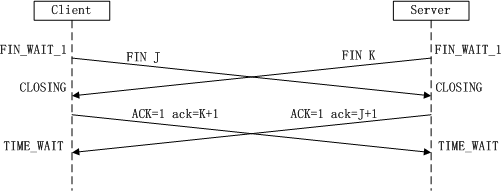
The process and status are already very clear in the above figure. We will not repeat them here. You can refer to the previous four wave analysis steps.
Fourth, notes
There are typical interview questions for three-way handshakes and four wave-offs. Here are suggestions for students who need it:
(1) What is the three-way handshake or process? Four handshakes? The answer to the previous analysis is.
(2) Why is the establishment of a connection a three-way handshake, but the closure of the connection is four waves?
This is because the server in the LISTEN state receives the SYN packet that establishes the connection request and puts the ACK and SYN in a packet and sends it to the client. When the connection is closed, when the FIN message of the other party is received, it only means that the other party no longer sends data, but it can also receive data, and not all of its data is sent to the other party, so you can close it immediately, or you can send some After the data is given to the other party, the FIN message is sent to the other party to indicate that they agree to close the connection. Therefore, the ACK and FIN are usually sent separately.
2.00mm Female Header Connector
2.00Mm Female Header Connector,Single Row 2.00Mm Female Header Connector,Smt Stand-Up 2.00Mm Female Header Connector,Vertical Type 2.00Mm Female Header Connector
Shenzhen CGE Electronics Co.,Ltd , https://www.cgeconnector.com