You may have heard that smart contracts on Ethereum run in a sandbox. So what exactly is a sandbox?
1. Why do we need a sandbox mechanism?
By default, an application can access all resources on the machine, such as CPU, memory, file system, network, and so on.
However, this is not safe. If you manipulate resources arbitrarily, it may destroy resources being used by other applications, or cause data leakage. To solve this problem, there are generally two solutions:
(1) Assign an account with limited permissions to the program: use the permissions management mechanism of the operating system to limit
(2) Provide a restricted operating environment for the program: this is the sandbox mechanism
2. What is the sandbox mechanism?
As mentioned above, a sandbox is a runtime environment that restricts an application's access to system resources.
Sandboxes are often implemented in virtual machines (VMs), such as Java's virtual machine JVM, Javascript's virtual machine V8 engine, Android's virtual machine Dalvik/ART, and Ethereum's virtual machine EVM, etc. The specific implementation methods are different. This article focuses on analyzing the sandbox mechanism implementation of JVM and EVM.
3. JVM sandbox mechanism
The sandbox mechanism of the JVM can be roughly divided into three layers:
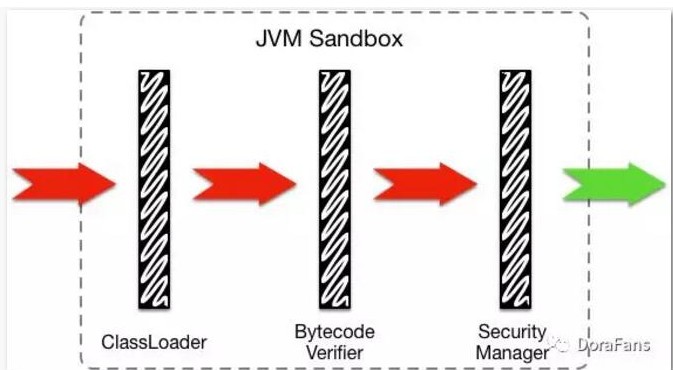
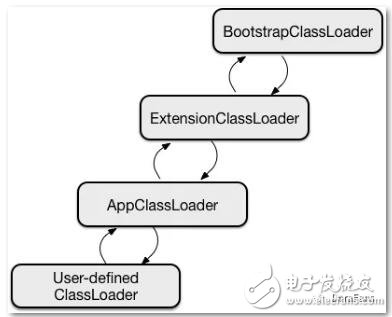
The first layer: class loader
Using the parent delegation model, when the low-level class loader receives a class loading request, it needs to first delegate to the high-level class loader area to complete, and only when the high-level class loader cannot complete the request will it be re-delegated to the low-level class loader. . Through this mechanism, it is ensured that the core classes of the system will not be tampered with, and malicious code cannot access key resources.
Layer 2: Bytecode Checker
After the class bytecode is loaded, it needs to be checked at the bytecode level, including the following:
(1) Variables should be initialized before use
(2) The method call must match the object reference type before
(3) The rules for accessing private data and methods are not violated
(4) Access to local variables falls on the runtime stack
(5) The runtime stack does not overflow. This mechanism ensures that the bytecode conforms to the Java language specification and avoids invalid access or out-of-bounds access.
Layer 3: Security Manager
This layer is maintained by application developers, who can formulate corresponding security policies according to their own needs. The default security policy configuration is located in the following two configuration files:
· $JAVA_HOME/conf/security/java.security
· $JAVA_HOME/conf/security/java.policy
By default the security manager is not enabled, you can add a parameter to the command line to enable it:
java -Djava.security.manager SandboxTest
The default security policy configuration does not allow applications to read and write files, so if you try to write a file, the runtime will report the following error:
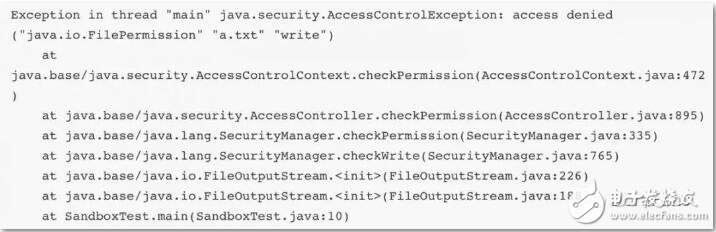
If you want to open this permission, you can write your own security policy file, for example, we write a my.policy:
Then you can specify this policy configuration at runtime:
java -Djava.security.manager -Djava.security.policy=. /my.policy SandboxTest
Application developers can make fine customizations for different application scenarios, and control the access rights of programs to the network, files, properties, etc.
4. Sandbox mechanism of EVM
EVM itself is a relatively closed environment and does not support direct access to the network and file system. From this perspective, it has already played a part of the sandbox function:
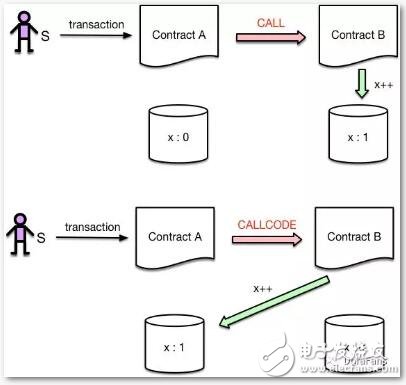
In addition, when smart contracts call each other, the EVM will reallocate the stack and memory space, and run the new contract in a brand new environment. A sandbox environment.
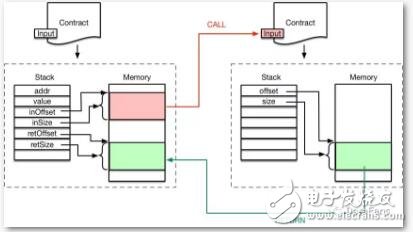
Finally, the storage of each smart contract is also independent of each other, and developers can limit the storage space that the contract can access according to their needs to avoid unauthorized access or modification. For example, the following figure describes the difference between CALL and CALLCODE instructions for memory access:
Adopting KN95 grade anti-particulate matter filtering technology and antibacterial environmental protection fabnc, effectively filtering and protecting from PM2.5 air particulate matter and bacteria. without breathing valve.
Adopting KN95 grade anti-particulate matter filtering technology and antibacterial environmental protection fabnc, effectively filtering and protecting from PM2.5 air particulate matter and bacteria. without breathing valve.
(Details
NIOSH Approved: KN95
FDA Cleared
Helps protect against certain airborne biological particles
Fluid resistant and disposable
Features include:
NIOSH approved KN95
Meets CDC guidelines for Mycobacterium tuberculosis exposure control
99% BFE (Bacterial Filtration Efficiency)
Fluid resistant
Collapse resistant cup shape design
Braided headbands, cushioning nose foam, and light weight construction for comfortable wear)
N95 Mask,Surgical Mask,Earloop Face Mask,Disposable Protective Mask
Guangzhou HangDeng Tech Co. Ltd , http://www.hangdengtech.com