In this morning's "News Tea Fan", Xiao Bian broadcasts questions about the "ME" vulnerability with Intel's management engine. Maybe after many small partners saw it, they thought that this relationship with the average user is not big, far from Windows or Office, and the emergence of Bug is terrible. In fact, it is not so simple (the general small problem is that the small series will not take the time to do the content).

As long as your computer is using an Intel processor, it may now be subject to serious security threats. This is not alarmist. A few years ago, Intel began to support the ME management engine (full name: Management Engine), which is responsible for managing and coordinating many modules within the processor. Why use "ME" management? Old players (when the age of the storm arrives) should remember that many years ago the motherboard was divided between South and North Bridges. Intel integrated the functions of the motherboard's North Bridge chip into the processor. The processor forms a nearly complete functional chip instead of a traditional "processor" (just as Qualcomm puts its Opteron processor now called the "platform").
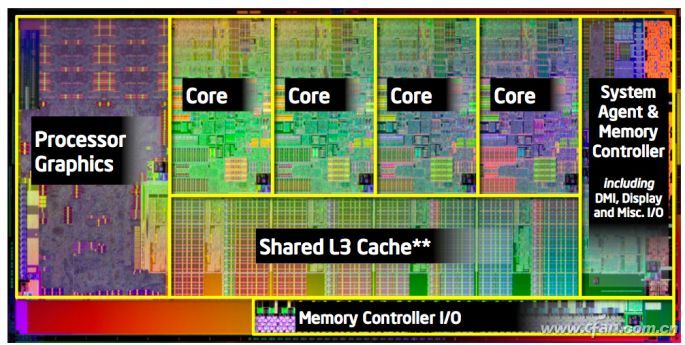
"ME" contains an ultra-mini system called MINIX. It has its own processor core and its own firmware in the Intel processor. It is in a completely independent state, and we can't see or operate, and the operating authority is extremely high. . What is the high point? Before the system started, it was already running. Even if the computer was in a shutdown or hibernation state, it was running uninterruptedly to perform processor (and chip) management, including some chip-level security work.
The loophole is in it. For our average user, even if the Windows protection is to be the ultimate, it is just a room security, and the foundation has completely collapsed! To find out if your computer is a high-risk vulnerability, first reply to the message “ME Detection†on our WeChat public number interface to get a detection tool. After downloading and unzipping, find "Intel-SA-00086-GUI" and double click to run.
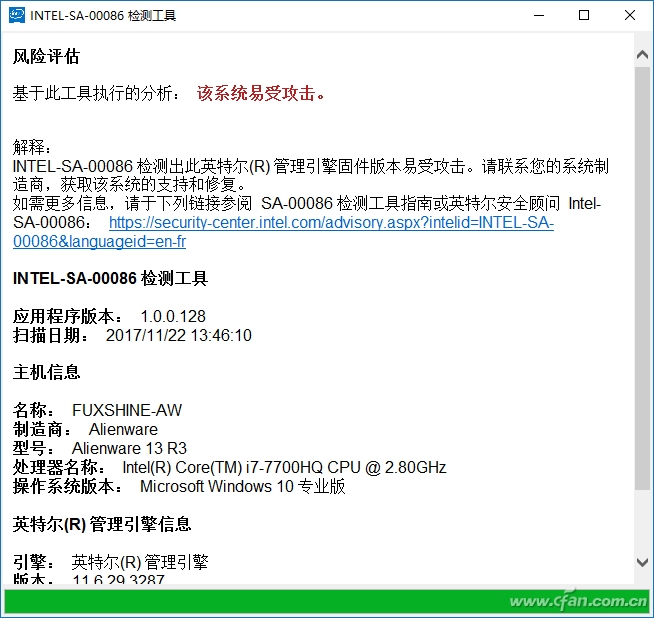
If "This system is vulnerable" is displayed, it indicates that there is a ME administrative engine vulnerability in the system. Otherwise, it shows that "this system is not vulnerable to attack." At present, from the sixth generation of Core processors (six generations of Corelake Skylake, seven generations of Core Kaby Lake, and eight generations of Core Coffee Lake), even the concurrent Xeon, Celeron, and Atom processors are all recruited.
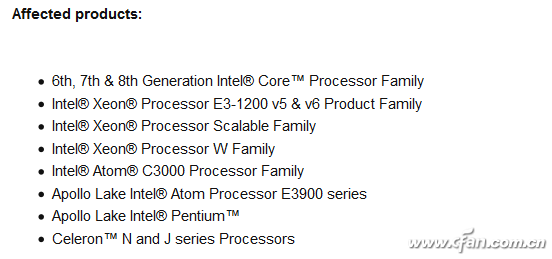
It is understood that the vulnerabilities that have been discovered can be used to load and execute arbitrary code, which can lead to system instability or even crashes in related PCs, servers, and IoT devices. And all this is built outside the operating system. Users simply do not have the ability to prevent.

It should be noted that there is no good solution for this issue. Xiaobian does not help by installing the latest version of the Intel Management Engine. According to Intel's message, the patch has been developed, but this requires brand machine manufacturers, motherboard manufacturers (DIY host) to help distribute the solution, which will take some time to resolve, Xiaobian will follow up at any time, once the news will share for everyone.
Ear Plugs,Bluetooth Earplugs,High Fidelity Ear Plugs,Noise Reducing Ear Plugs
GUANGZHOU LIWEI ELECTRONICS CO.,LTD , https://www.gdliwei.com